My Predictions for Apple’s Tablet Event Tomorrow
Unless you’ve been living under a rock, you are no doubt aware that Apple plans to reveal their “latest creation” tomorrow, January 27th, 2009. It is most likely their long awaited iTablet/iSlate/iWhatever. I’ll be following Engadget’s live blog of the event tomorrow.
It is also my birthday tomorrow, but I don’t care as much about that. I just want to know what Apple’s been doing all this time and what they’re going to announce. I’m pretty sure that makes me nerdy, among other qualifications.
These are my tablet related predictions, which I will update with the results:
- Apple will announce a tablet device of some kind.
- It’s name will begin with a lower case I. I have to get at least one correct, right? I’ll guess iTablet. I don’t think they’ll do iSlate.
- The device will not have an e-ink screen.
- The device will not have an AMOLED screen.
- It will be a conventional LCD screen with LED backlighting.
- It will not run full OS X. Only a subset will be allowed, such as Safari, etc. Only apps from an app store will be allowed.
- There will be a tablet app store.
- There will be backwards compatibility for iPhone apps running in some kind of emulation mode.
- There will be a innovative text input method. I can’t speculate as to what it will be, but knowing Apple, it will be good.
- Its battery life will be expressed in hours, not days or weeks, unlike the Kindle or Nook.
- Verizon will be announced as a 3G data partner for the tablet device.
- The tablet will sell like hotcakes at first because Apple made it, but I think this will be a fad device and perhaps regarded as Apple’s second flop (see Newton). I am putting this down “on paper” because I think it will be funny if I’m completely wrong and I can read my own words in a year or so.
My other predictions for the event are as follows, which I will also update with results:
- No new iPhone will be announced.
- No AT&T exclusivity related announcements will be made (this will be saved until WWDC in June).
- Incremental changes will be made for the iPhone OS, perhaps allowing some sort of rudimentary multitasking, perhaps in a 3.5 or 4.0 revision of the OS.
Additionally, I am aware that I haven’t blogged in 5 months. I’ll be following up on this post with some sort of recap explaining what I’ve been doing.

 A
A 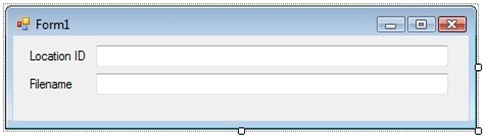
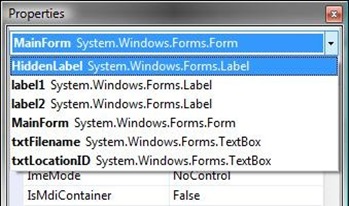
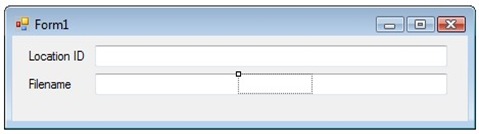 The hidden control becomes highlighted. Click into the title bar of the form. Press the menu key on your keyboard to display the context menu.
The hidden control becomes highlighted. Click into the title bar of the form. Press the menu key on your keyboard to display the context menu.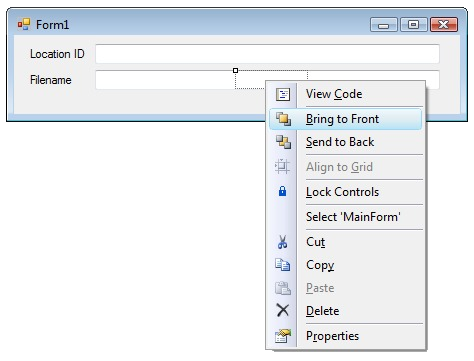
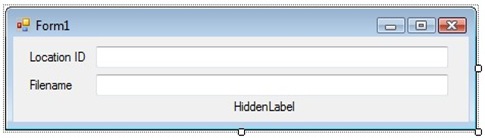 As you can see, the control that was previously hidden is now visible and has been moved.
As you can see, the control that was previously hidden is now visible and has been moved.

